Android 11 will harden hidden API restrictions and remove meta-reflection bypass
For those of you not in-the-know, Google introduced a rather annoying change in Android 9 Pie that concerns enthusiast developers looking to push the boundaries of what’s possible in Android. I’m talking, of course, about the addition of the hidden API blacklist. With the intent to promote application stability, Google blocked access to most hidden APIs – APIs that exist in the Android framework but are undocumented in the Android SDK. These APIs could be accessed via reflection until Android 9 Pie, and currently, can still be accessed using the meta reflection workaround.
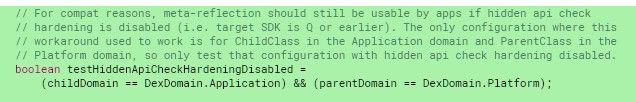
If you have no idea what I’m talking about, you should probably read the article I wrote a few months ago on this subject. It’ll explain everything you need to know about meta reflection and how it works. Unfortunately, it looks like Google took notice of this workaround (whoops). In a new commit to AOSP, Google has introduced code to “harden” Android’s hidden API checks. This basically means meta reflection will no longer work.
Of course, this won’t affect all apps. Just like with the original API blacklist, only apps targeting Android 11 (API level 30) or later will be affected. You can still target API level 29 or lower and use meta reflection. With the Play Store’s progressively increasing minimum target SDK requirements, though, this won’t be a valid workaround for long.
At this time, I don’t know of any workarounds for apps targeting API 30. Android 11 is a long way off, though, so there’s a good chance that someone will find a way to restore access. In the meantime, if you’re using hidden APIs, you may want to file a request for them to be made public in Android 11. If you’re good at analyzing C++ and Java, and you want to take a stab at “fixing” this little blacklist situation, take a look at the relevant commit.
The post Android 11 will harden hidden API restrictions and remove meta-reflection bypass appeared first on xda-developers.
from xda-developers https://ift.tt/2TO7lpV
via IFTTT
No comments: